The Critical Role of Cybersecurity in Fire Safety Voice Communication

Cybersecurity in fire safety has become a critical concern for infrastructure owners, especially in high-risk environments. Public address and voice alarm (PAVA) systems are no longer isolated infrastructures. Most PAVA systems are IP based and very often integrated with other security and safety systems to provide real-time alerts, automated responses, and remote management capabilities.
While these interconnected PAVA systems enhance safety and efficiency of people and businesses, as with any IP based security and safety systems, they also become more attractive targets for cybercriminals.
Vulnerabilities are further increased by the requirement to access cloud-based services and the growing demand for remote control / monitoring.
However, the unique challenge of a PAVA system comes from the fact that they operate in high-risk environments, particularly at sites of national importance, such as transportation hubs, public venues, and government buildings, and this makes it more attractive targets for cybercriminals.
Unlike traditional IT infrastructure, public address systems are often in public spaces, making them even more accessible and prone to attacks.
Cyberthreat Landscape of PAVA

Fire safety voice communication systems such as a PAVA system is designed to function reliably during emergencies and help people evacuate the building in case of a fire emergency.
Without robust cybersecurity measures, malicious actors could gain unauthorized access to the system, potentially sending false evacuation messages, disabling alarms, or intercepting sensitive information, causing confusion and panic.
The following are some of the potential attacks of a PAVA system:
- Gain unauthorized access to PAVA system make false announcements or other propaganda messages and create confusion and panic among recipient of the broadcast
- Evade and disable all broadcasts, bringing the daily operation into a standstill
- When a PAVA has a microphone such as a noise sensor, hackers can use it to spy on users by listening into the microphones.
- Due to easy access of PAVA system, hackers use PAVA system as a gateway to gain access to other systems or launch denial of service attacks.
In a recent case, hackers targeted municipal public address systems in Jerusalem and Eliat, triggering the air raid sirens systems throughout both cities, causing chaos and panic. This incident underscores the urgent need to secure fire safety voice communication systems against cyber threats. Taking a proactive approach to cyber security will enable security system owners to avoid damaging and disruptive cyber-attacks.
Cybersecurity Vs. Cyber Defence
Cybersecurity and cyber defence represent two interconnected disciplines focused on protecting critical digital assets and infrastructure such as PAVA.
Cybersecurity refers to the broad practice of protecting systems, networks, and data from unauthorized access, cyberattacks, damage, or theft. Cyber defence is a subset of cybersecurity, focusing specifically on detecting, responding to, and recovering from cyber threats and attacks.
Think of cybersecurity as the fortress walls designed to keep threats out, while cyber defence is the guards inside the fortress, constantly monitoring for intruders, ready to respond if someone breaches the wall.
While differing in scope, cybersecurity policies and cyber defence capabilities work closely together to establish layered protection and are essential for a robust security posture, especially in critical systems like PAVA where both preventive and responsive measures are crucial.
Defence-in-Depth: A Layered Approach to Cyber Protection
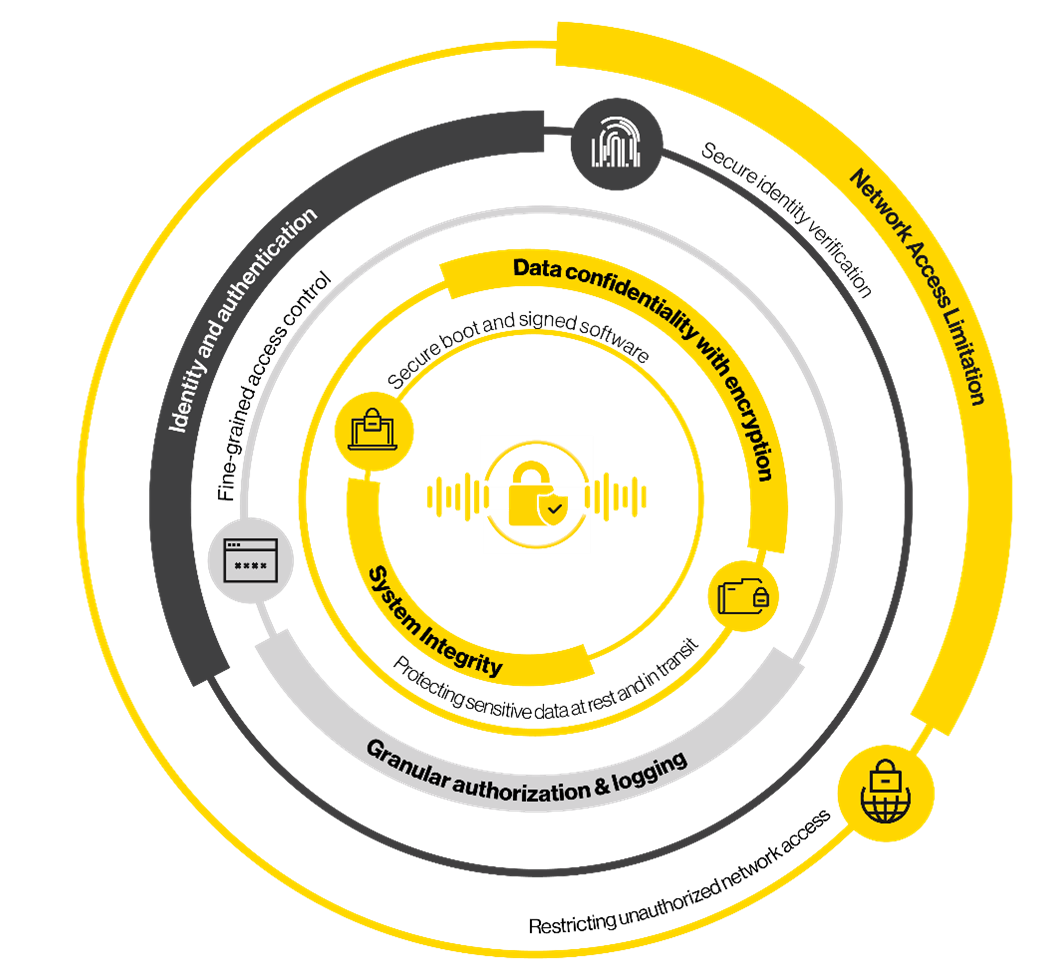
Cyber defence is the coordinated practice of protecting software, systems, or component on an IP network, including critical systems such as the PAVA system from cyber-attacks by reducing the ‘attack surface’.
An ‘attack surface’ is defined as the total number of all possible entry points for unauthorized access into any system. It includes all vulnerabilities and endpoints that can be exploited to carry out an attack.
No single measure is ever going to be enough to secure an enterprise against the complex and evolving cyber threat landscape. Defence in Depth (DiD) is an approach in which a series of defensive mechanisms are layered in order to provide additional protection.
If one mechanism fails, other steps up immediately to thwart an attack. An effective cyber defence detects, prevents, and reports cyber-attacks using key technologies and best practices.
Network Access limitation
Restricting unauthorized network access and reducing the attack surface with port security. A port is a virtual or physical point where network connections start and end. Ports are software managed by a computer's operating system allow use to implement Port security. Port Security helps secure the network by optionally disabling unused Ethernet ports and monitoring others. Active monitoring helps detect and raise alarms if links are temporarily removed.
Identity management and authentication
This ensures secure identity verification for users, devices, and applications. Technologies such as multifactor authentication (MFA) adds an extra layer of security beyond passwords reduces the risk of unauthorized access. “Never trust, always verify” principle should be adopted regardless of whether a user or system is inside or outside the network.
Granular authorization & logging
Implementing fine-grained access control, enforcing least privilege, giving user accounts or processes only those privileges which are essentially vital to perform its intended functions. This is an additional layer of protection to reduce the attack surface. In addition, logging all security-relevant events for threat detection.
Data confidentiality with encryption
Encryption in cyber security is the conversion of data from a readable format into an encoded format. Encrypted data can only be read or processed after it's been decrypted. Protecting sensitive data at rest and in transit must be a key focus.
System Integrity
Ensuring system integrity from the initial boot process, preventing tampering, and verifying software authenticity.
Continuous Monitoring and System Auditing
Cybersecurity in fire safety isn’t just about prevention, it’s also about detection and response. Advanced PAVA systems now include continuous auditing features, generating comprehensive logs (syslogs) with metadata such as:
This data is essential for forensic analysis and quick remediation in case of an incident.
Future of cybersecurity for regulated communications
The importance of minimizing the potential interruption to essential services such as PAVA is obvious and well understood across all industries, as this will have serious consequences.
As fire safety voice communication systems evolve, integrating cybersecurity from the ground up is essential. This requires collaboration between fire safety professionals, IT security experts, and regulatory bodies to develop comprehensive security frameworks.
Investing in cybersecurity is not just about compliance; it’s about ensuring that critical safety systems are resilient, reliable, and ready to perform when lives are on the line. By prioritizing cybersecurity, we can build a safer, more secure future for all.
For a timeline of significant cyber incidents since 2006, go to: Significant Cyber Incidents | Strategic Technologies Program | CSIS
